Secure Crypto Access with Trezor Login and Multi-Signature Support
Understanding Trezor Login: Hardware-Based Security First
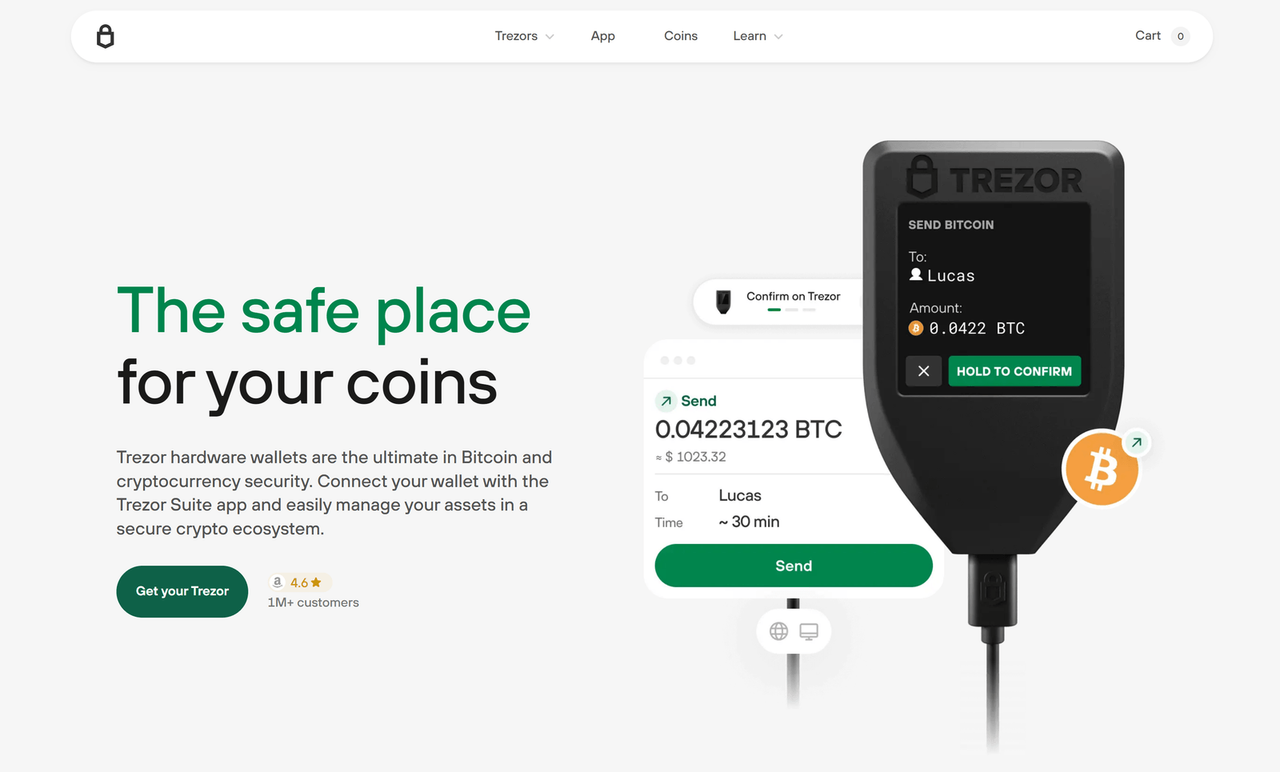
Trezor login is one of the most secure ways to access cryptocurrency wallets and blockchain platforms. By using a physical Trezor device like the Model One or Model T, users can authenticate themselves without exposing private keys to the internet. Unlike browser-based logins, Trezor login uses hardware-level protection to safeguard digital assets.
When a user initiates login via Trezor, the process requires physical interaction. The Trezor device must be connected via USB, and any login attempt must be confirmed on-screen. Whether you're accessing Trezor Suite, web wallets, or dApps via MetaMask, Trezor login adds a critical layer of verification to prevent unauthorized access.
Made in Typedream